As part of the Cyber Essentials Plus certification, you are required to undergo a credentialed vulnerability scan, using an account which has local administrator/root access to the machine.
For InfoSec Governance audits, we utilise the vulnerability scanner Nessus Professional when performing the audits onsite and recommend that our customers use this as well (or Nessus Essentials is auditing remote users).
As Nessus requires quite a bit of configuration within the environment to work as needed against the newer Operating Systems, we recommend that you test to ensure that the scan works accordingly and doesn’t cause any delays to your audit.
We have written articles on how to configure a Windows environment as well as a MacOS environment, this can take some time to reconfigure and is recommended to tweak as soon as you start the Cyber Essentials Process.
Note: If we are unable to perform a credentialed vulnerability scan, it will be a failure of the audit, or will delay the audit until it can be successfully completed.
If you already have and use a vulnerability scanner within your business. As part of the Cyber Essentials Plus audit, we, as certification bodies, are allowed to use the following authorised scanners. If you have a vulnerability scanner which meets the PCI ASV requirements, them you can use one of the following providers for testing.
- Tenable
- Qualys
- Saint Corp
- Edgescan
- Outpost24 AB
- Clone Systems
- Magaplan IT
- AKATI Consulting (M) Sdn Bhd
Which Nessus version shall I use?
Working from the office
If you are working from the office and most of your staff are working in the office as well, we will recommend that you download Nessus Professional from the Tenable website and install it on one machine which can see all the servers and workstations.
Working remotely/from home
If your staff are working remotely or don’t have an office, we will recommend that you download Nessus Essentials from the Tenable website, this will need to be installed on all the machines which are being audited in the sample set.
Download and configuration
You can download the Nessus vulnerability scanner from: https://www.tenable.com/downloads/nessus?loginAttempted=true,choose the file that best suits the environment. Both Nessus Professional and Nessus Essentials are the same file, the activation code which you enter after installation, states which version you will be using.
Once you have downloaded the correct version, you will need to install the product and follow all the prompts when requested.
During the installation, you will receive a message similar to the below, click on the Advanced button
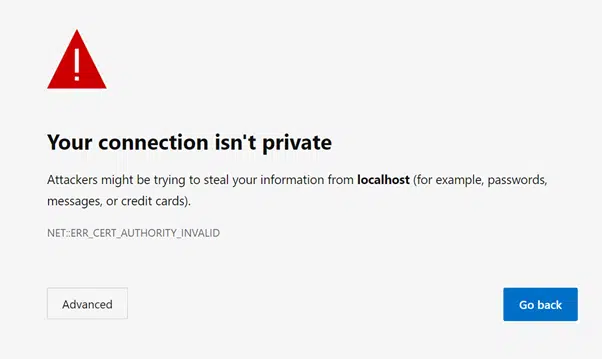
Then click on ‘Continue to localhost (unsafe)’
Select ‘Nessus Essentials’, even if you are running this in your office, we will change the activation code on the day of the audit.
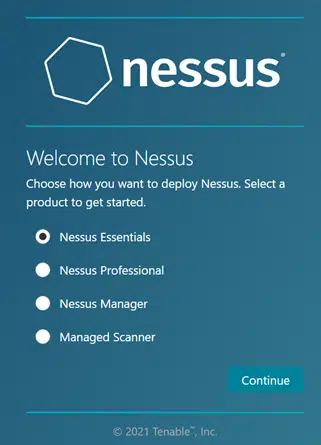
Click continue to continue with installation and fill in the information to generate an activation code.
If you don’t receive a code after a while, go to https://www.tenable.com/products/nessus/activation-code instead and click on ‘Register Now’ under Nessus Essentials.
Once you have the activation code, paste it into the text box and click continue.
Next create a new user account and make a note of it as you will need to use to access Nessus later.
The next stage will download and configure the plugins in preparation for the scanning, this can take quite a long time depending on the bandwidth and system requirements of the machine.
Create a scan
If you have closed the window after installation, navigate to https://localhost:8834/ and login to Nessus.
If you see this window, close it.
Next, click on the blue ‘New scan’ button at the top right of the screen.
Next, click on the ‘Advanced Scan’ scan option
Next, fill in the general information, give your scan a meaningful name and enter the targets to scan, if you are just scanning your local machine, you can enter localhost, or if you are scanning a network you can enter the network range as shown below.
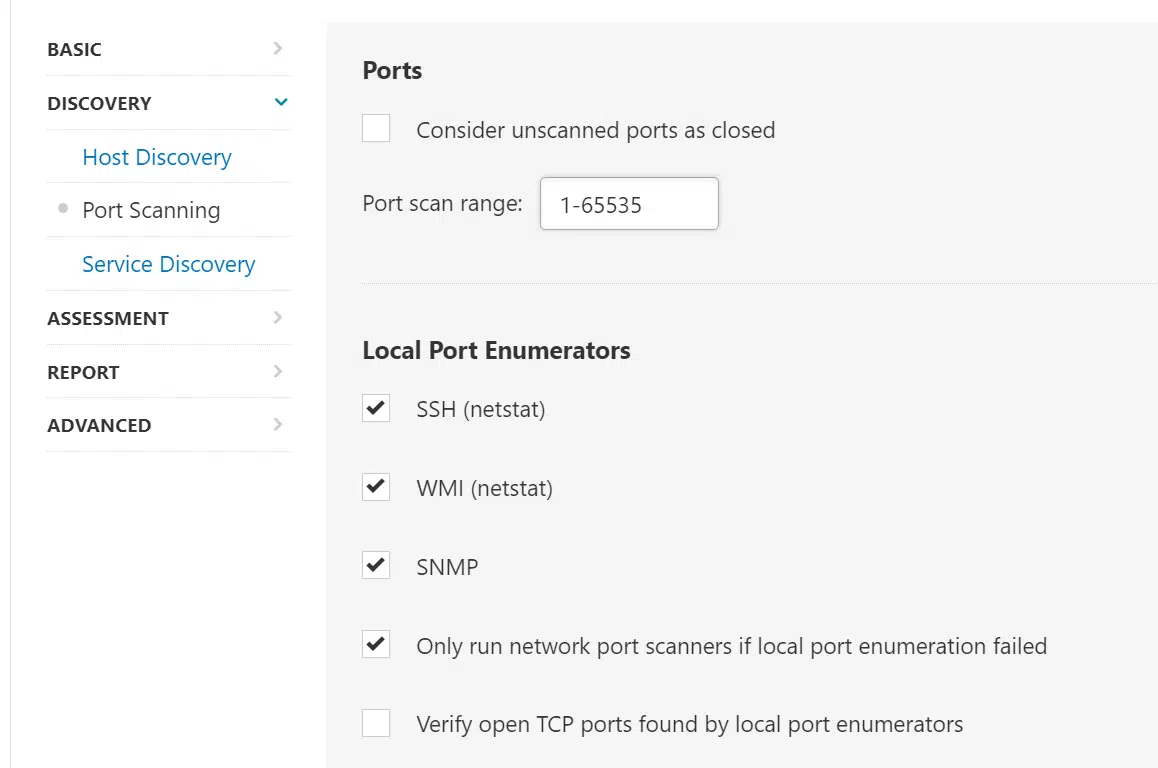
Next click on ‘Discovery’ on the left side and select ‘Port Scanning’. Change the ‘Port Scan range’ from the default value of ‘default’ to ‘1-65535.
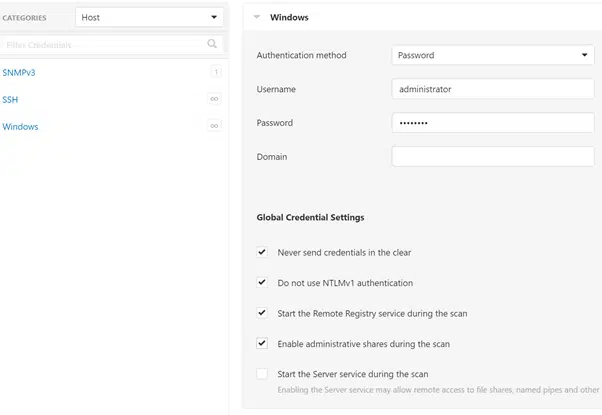
Next, click on the ‘Credentials’ tab then click on ‘Windows’ for scanning Windows machines, or ‘SSH’ for MacOS and Linux machines.
If you are using Windows, enter in the credentials which have local administrative access as shown below. Also ensure that the ‘Start the Remote Registry Service during the scan’ option is checked along with ‘Enable administrative shares during the scan’
Once all set, click on the Save button and then click back to ‘My Scans’, to list the scans which have been configured.
To start the scan, click on the play type button.
Review scan results
Once the scan has completed, you can click on the scan and view the results. You need to ensure that you have no CVSS findings which are 7.0 or above. This can be done by creating a filter against ‘CVSS base score 3.0’ and ensuring that you only list scores greater than 6.9.
If however, you get something like the below screenshot, the credentialed scan has not worked.

To make sure your scan worked, you should see something similar to the following, where you have information about (credentialed check) as well as listing all the software installed on your device: