How to setup your Windows environment for a Nessus Credentialed patch scan
If you are reading this you may be undergoing a Cyber Essentials Plus audit, which requires you to undergo a credentialed patch scan, one of the products which can be used is Tenable Nessus.
Your Cyber Essentials certification body may have asked you to configure your environment in preparation for this, this is a requirement and failure to not have a successful credential patch scan will result in your audit failing.
This guide walks you through the process of configuring your environment in preparation for an audit. There are several parts to this configuration and this guide will concentrate using the group policy management tool as a way of configuring the environment. All the configuration settings can be added to the one Group Policy Object.
If you don’t have Active Directory, then you can configure all your machines locally using the Local Group Policy Editor functionality.
This guide also assumes that you are using the built in Windows firewall, if you are using another endpoint firewall such as that from your Antivirus vendor, then add exceptions accordingly.
The steps to configure the environment are as follows:
- Create a dedicated Nessus administrator account which has full local access to Windows machines.
- Ensuring network profile is configured as ‘Private’
- Allow WMI access through the firewall
- Allow File and Print Sharing through the firewall
- Create a ‘LocalAccountTokenFilterPolicy’ registry entry
- Configure Remote Registry service
Creating dedicated Nessus account
Create a domain user and group and name them accordingly, then make the new user is a member of the new group.
Expand your GPO and go to Computer configuration -> Windows Settings -> Security Settings -> Restricted Groups, right click and select ‘Add Group’ and select the group you have just created. This will open up the below screen, add the group, if its not already there then select the button Add button and add ‘builtin\administrators’.
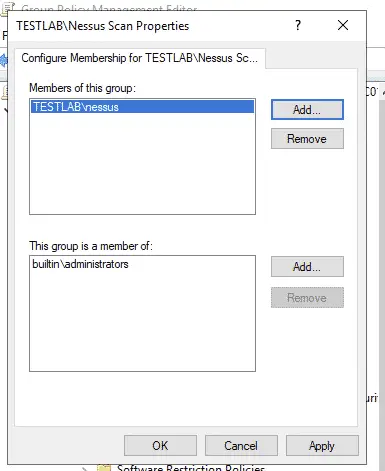
Click OK to save.
Ensuring network profile is configured as ‘Private’
Expand your GPO and go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Network List Manager Policies. Select the network that are using within your business, by default this will be ‘Network’. Click on the ‘Network Location’ tab and then change the location type to ‘Private’.
Once changed, click ok to save.
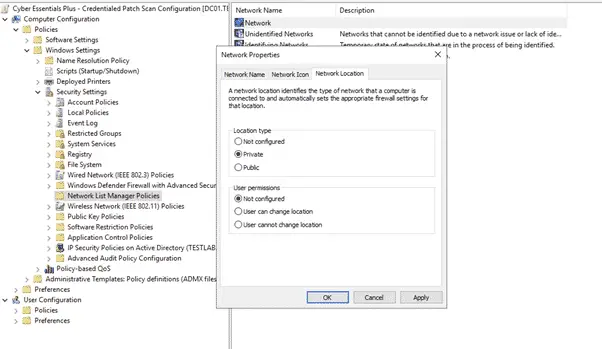
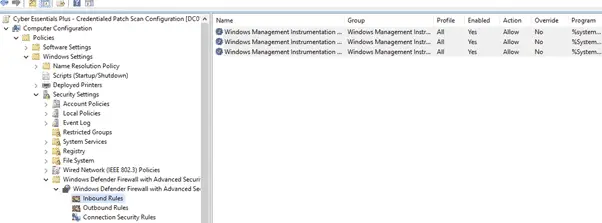
Allow WMI access through the firewall
Go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security. In the right pane, expand Windows Firewall with Advanced Security until Inbound Rules visible. Right-click on it.
- Choose New Rule …
- Select Predefined and Windows Management Instrumentation (WMI) in the list
- Click Next
- Tick all the Windows Management Instrumentation-rules in the list (usually 3 pieces)
- Click Next
- Select Allow the Connection
- Click Finish
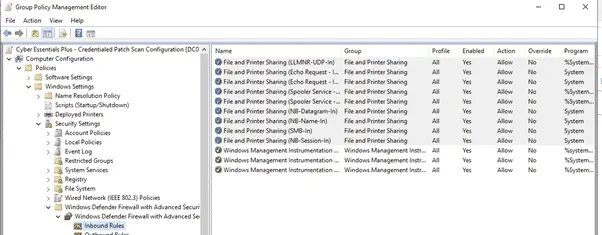
Allow File and Print Sharing through the firewall
Go to Computer Configuration -> Policies -> Windows Settings -> Security Settings -> Windows Firewall with Advanced Security. In the right pane, expand Windows Firewall with Advanced Security until Inbound Rules visible. Right-click on it.
- Choose New Rule …
- Select Predefined and File and Printer Sharing in the list
- Click Next
- Tick all the Windows Management Instrumentation-rules in the list (usually 3 pieces)
- Click Next
- Select Allow The Connection
- Click Finish
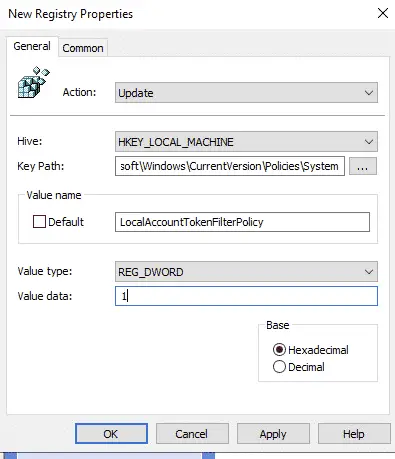
Create a ‘LocalAccountTokenFilterPolicy’ registry entry
Go to Computer Configuration -> Preferences -> Windows Settings -> Registry, right click on the right pane and select new -> registry item.
- For the Key path enter: \SOFTWARE\Microsoft\Windows\CurrentVersion\Policies\System
- For the value name enter: LocalAccountTokenFilterPolicy.
- For the value type, change to: REG_DWORD
- For the value data enter: 1
Click OK to save.
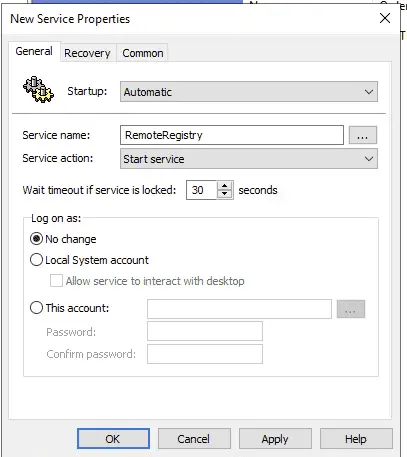
Configure Remote Registry service
Go to Computer Configuration -> Preferences -> Control Panel Settings -> Services, right click on the right pane and select New -> Service.
- Change Startup to Automatic.
- Select the Service name: Remote Registry
- Change Service Action to automatic
- Click Ok to save
And that’s it, once one wait for the changes to propagate around your environment. This will require a computer restart to take effect. You should then be ready for your certification body to perform a scan using Nessus.
