What is SMB Signing and do I need it?
SMB signing helps secure communications and data across the networks, there is a feature available which digitally signs SMB communications between devices at the packet layer. When you enable this feature the recipient of the SMB communication to authenticate who they are and confirm that the data is genuine. This can help safeguard against attacks such as man-in-the-middle (MITM) attacks.
Server Message Block (SMB) is a file protocol used within Windows, Linux and other storage devices. SMB allows devices to have the ability to share and store files easily and allow devices and/or people to access these said files. SMB has been around for a great many years and Microsoft have been trying to ensure that the first version of SMB is no longer used due to inherent security risks as well as there are newer versions available that do a lot more.
There is one problem, however, although SMB signing is available on all versions of Windows, it’s currently only enabled on Domain Controllers. If you, the business, want to enable this feature you must specially enable it within Group Policy (or the Local Security Policy). In larger organisations, it’s recommended that this is enabled on all devices as it helps protect information and reduce the chances of information leakage or additional attacks.
Enabling SMB Signing
Signing under SMBv1 is different to the later versions, for the purpose of this blog article we won’t discuss how to enable signing under SMBv1 as we’re looking to move away from this. However, configuring SMB signing for SMBv2 and above you need to do the following:
To start, open the Group Policy Management tool, this can be done either through Server Manager > Tools > Group Policy Management or by running ‘gpmc.msc’ in PowerShell or Command Prompt. Then, depending upon your preferences, either create a new Group Policy or edit an existing one.
Once your group policy is in edit mode, navigate to Computer Configuration > Policies > Windows Settings > Security Settings > Local Policies > Security Options.
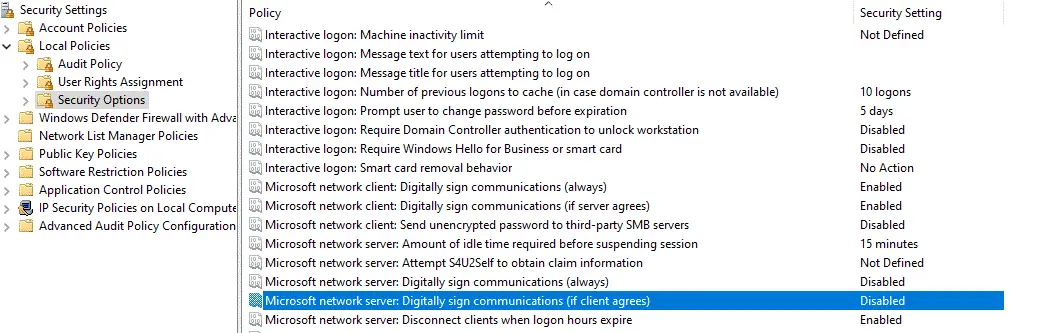
There are 4 policy items that you will need to look at, all these policy items can either be enabled or disabled.
SMB Server Packet Signing
The following two policy items apply to the SMB server that is hosting the files or to say that it is Windows systems that serve any files or printers for communications over SMB to clients within the network.
Microsoft network server: Digitally sign communications (always)
This policy option is to control whether the server requires packets, it checks to see whether SMB packet signing must be negotiated before further communication with an SMB client is allowed.
This is set by default as enabled for domain controllers but disabled for other member servers within the domain.
Microsoft network server: Digitally sign communications (if client agrees)
This policy option will determine whether the server will negotiate SMB packet signing with clients that request it. When enabled, the server will negotiate SMB packet signing as per the request of the client. If SMB packet signing is enabled on the client then it will be negotiated by the server.
SMB Client Packet Signing
The following policies apply to the SMB clients, that is any Windows devise that establish a connection to an SMB server.
Microsoft network client: Digitally sign communications (always)
This policy ensures that the SMB client will always require SMB packet signing when enabled. If the server does not agree to support SMB packet signing with the client, the client will not communicate with the server.
Microsoft network client: Digitally sign communications (if server agrees)
This policy is enabled by default and determines whether the SMB client attempts to negotiate SMB packet signing with the server.
