Today we’re going to talk about Microsoft LAPS. As I’m sure you know, password management within an enterprise environment can be difficult, more so when you consider the management and controlling of local administrator accounts across all Windows devices. Ensuring that everyone is using their computers with normal low-level privileged accounts can be a challenging task, more so when you need to ensure that any local administrator passwords should be secure and yet managed easily.
A lot of people will simply use the same password for all local administrator accounts, which can allow the management of machines to be frighteningly easy, however what happens if one machine is breached and the local credentials are dumped and then broken? The attacker has access to the whole estate. This is where Microsoft LAPS comes into play.
What is Microsoft LAPS?
Microsoft Local Administrator Password Solution (LAPS) is a password manager that when configured is integrated into Active Directory. LAPS allow domain administrators and/or help desk staff to manage and rotate passwords for local administrative accounts across all Windows devices. Having this tool setup within your Active Director environment is a great way to ensure that if anyone gains access to an endpoint that any lateral movement is restricted due to having unique passwords across all endpoints.
Another benefit of using LAPS is that it is not reliant upon additional computers, applications or services to manage these passwords, once setup its tightly integrated into Active Directory, thereby allowing you to integrate and manage passwords in AD compatible tools.
You can read more about Microsoft LAPS here and you can download the installation package here.
How to setup Microsoft LAPS
Before we begin, there’s a small disclaimer up front, installing and configuring LAPS is not as simple and download and execute a setup application, there is some manual configuration which is required using PowerShell and Group Policy. If you aren’t sure what these are or how to use them, Microsoft does have some good documentation on installing and setting up LAPS, check out the ‘LAPS_OperationsGuide.docx’ document for more information. Note: You will need to be an AD Schema administrator for some parts of the setup process.
Once you have downloaded the LAPS installation application, run the application on a domain controller, you will be asked if you want to install the following items.
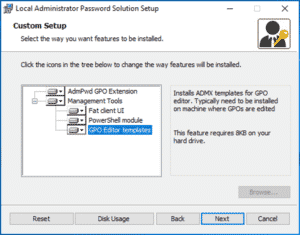
In this example, we’re going to select all items (for endpoints you only need to push out the ‘Adm GPO Extension’). Go ahead and install the features.
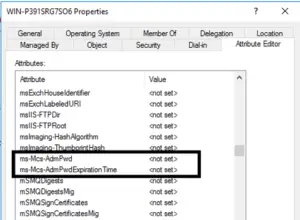
Once installed, the next step is to extend your Active Director Schema to allow the support of LDAPS. Microsoft provides a PowerShell module that will take care of this process (make sure you are an Active Directory Schema Administrator when running this). There will be two computer attributes added to your schema these are: ‘ms-Mcs-AdmPwd’ which stores the local administrator password and ‘ms-Mcs-AdmPwdExpirationTime’ which stores the time until the password expires.
Launch a PowerShell terminal and then import the ‘AdmPwd.ps’ module
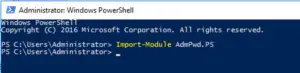
Extend the AD Schema

Once you have extended the schema you will see the two new attributes
Now, if you go into Group Policy management editor, you can configure LAPS.
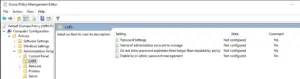
The ‘Password Settings’ GPO setting allows you to configure the password complexity for the passwords which are going to be used for the local administrator accounts, including the length and age.
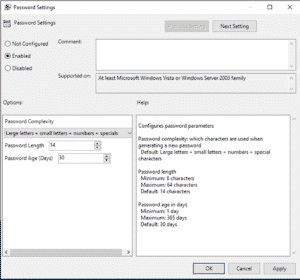
The ‘Enable local admin password management’ setting controls if the endpoints are governed by the GPO which are being managed by LAPS.
Securing LAPS
Now that you have configure LAPS to store passwords in Active Directory, you will need to ensure that you lock down the permissions appropriately. The Microsoft admin guide explains how you can do this.
Deploying AdmPwd GPO Extension to endpoints
Before you can manage all the endpoints with LAPS you will have to deploy the ‘AdmPwd GPO Extension’ to all endpoints, this can be done a number of ways, some of these are:
- Run the LAPS.x64.exe application on all endpoints and only install the GPO extension
- Copy and deploy the dll file across all machines
- Silently install the application via group policy
Managing passwords
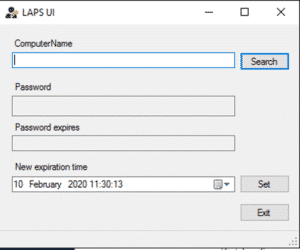
Once all set up, you can manage the passwords a number of ways, the easiest way is using the LAPS UI application, but you can also use PowerShell to manipulate the passwords.
I hope this article helps you learn and understand how to manage local administrative passwords more efficiently and securely than having the same password on every machine.
