Cyber Essentials scheme update – 24th April 2023
The owner of the Cyber Essentials Scheme, NCSC, and their official partner IASME Consortium announced on the 23rd January 2023 that there is an upcoming update to the Cyber Essentials Scheme. This continues on the back of the large update that was released back in January 2022.
The update will have the question set codenamed ‘Montpellier’ and will come into force on the 24th April 2023 and will not affect any assessments which have been started or are in progress before the update date. Any assessments which are undertaken from the date of the 24th April will need to comply with the new question set and the new updated Cyber Essentials Technical requirements document, version 3.1. This document can be found on the NCSC website at: https://www.ncsc.gov.uk/information/cyber-essentials-technical-requirements-updated-for-april-2023.
What’s changing?
So you may be asking, what’s changing? Are there any sweeping changes coming into place like the last update? We’ll you’ll be glad to know that this is a smaller update and with this update brings several clarifications on how to complete your assessments and how you should comply with the five technical controls.
The definition of ‘Software’ has been updated
The definition of software has now been updated to clarify where firmware is in scope of any assessment. From the 24th April, it will be defined that software includes Operating Systems, commercial off the shelf applications, plugins, interpreters, scripts, libraries, network software and firewall and router firmware. The new question set will no longer expect you to ensure that firmware is updated on all devices within scope of the assessment.
Bring Your Own Device (BYOD) advice updated
The NCSC has updated their guidance on the use of Bring Your Own Device (BYOD), this guidance can be found here: https://www.ncsc.gov.uk/collection/device-security-guidance/bring-your-own-device
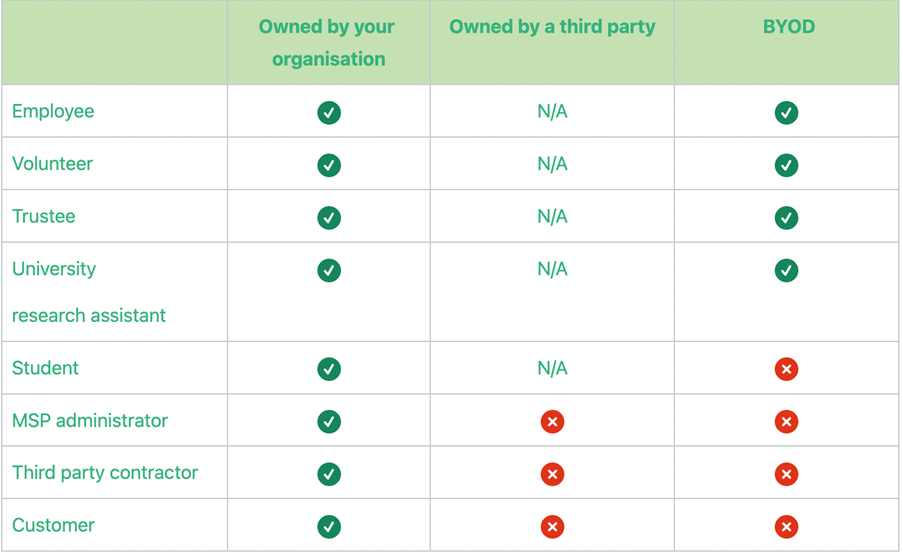
Further clarification on third-party devices
Within the Montepellier question set all end user devices that your organisation owns or are loaned out to a third-party must be included the assessment of the certification. A new table has been included which brings further clarity on this subject.
When it comes to any devices which are not owned by the organisation under assessment, the table listed below highlights what is in and out of scope.
Updated device unlocking section
The device unlocking section of the assessment has been updated to reflect that in some cases changes can’t be made as they are restricted by the vendor. When this is a case for you, you should use the default vendor settings.
What is an example of this? An example may be where you are using a device where there are no options to change the configuration settings to meet the requirements of Cyber Essentials. An example of this would be ensuring that your account lockout is set to 10 failed sign0in attempts, with Samsung devices, this is not possible to do as their default lockout is set to 15 with no ability to change this option. Therefore, under Cyber Essentials, you would go with this default configuration setting.
Updated Malware protection section
When it comes to antimalware protection, its always been defined that you must have anti malware software installed on all devices which are in scope of the assessment. It is recommended by Cyber Essentials that you use the default built in protection, where available over third-party products However this doesn’t mean you can’t use any third-party product to protect your systems.
The malware protection section has been updated to fall inline with new guidance, research and knowledge available.
In all cases, where antimalware software is being used, you should ensure that it is:
- Updated in line with vendor recommendations
- Prevents malware from running
- Prevents the execution of malicious code
- Prevents connections to malicious websites over the internet
When using the application allow listing control for protecting mobile applications, you should ensure that only approved applications, restricted by code signing, are allowed to execute on devices. You must:
- Actively approve such applications before deploying them to devices
- Maintain a current list of approved applications, users must not be able to install any application that is unsigned or has an invalid signature
Zero-trust architecture
Zero-trust hasn’t really been covered when it comes to the Cyber Essentials scheme, however in the new version there is new information on how Zero-trust architecture affects the Cyber Essentials controls and how it could affect your business when you look to become certified.
Zero Trust Architecture starts playing a bigger part of business operations when businesses start to work from home a lot more and start embracing cloud technologies more. With the boundaries of business networks spreading from the normal office based networks to more remote based and cloud based networks, now is more important than every to ensure that security and technology controls are in place to safeguard against new risks.
This is where zero-trust comes into place. It’s an approach whereby you design your environment to trust no one and no device and instead you verify each and every access request to business systems.
The NCSC have written some guidance about zero-trust architecture, this can be found here: https://www.ncsc.gov.uk/collection/zero-trust-architecture
Document realigning and necessary changes
Lastly, the technical requirements document and the self-assessment questionnaire have been redesigned to ensure that they match and align together. The requirements document has been written with place English instead of technical terms and accessibility has been further enhanced. The technical requirements document has also been updated to ensure that the requirements align with the question set, which is:
- Firewalls
- Secure Configuration
- Security Update Management
- User Access Controls
- Malware Protection
